Time for a Wireless LAN Assessment? Do you have Ghosts & Goblins?
October in Philadelphia is extraordinary; between the crisp dry days, vibrant fall colors, and eerie decorations covering houses with orange spooky carved pumpkins all over town, it's easy to get caught up in the Halloween spirit.
So, as I wondered what to say in my blog this week, I couldn't help but see monsters, goblins and ghosts everywhere! There are monsters quietly hiding inside every company; foul creatures in our very private wireless LAN’s. Ghouls so deadly, so insidious, they can attack your company data and steal it or corrupt it without your knowledge or consent! These demons, if you continue to let them run wild long enough, can destroy your IT systems and possibly your company. So in this ghostly Halloween time of year let’s focus in on an unseen and relatively misunderstood component of your IT infrastructure, your WiFi wireless LAN.
What better way to focus in on your WiFi wireless LAN than through shining a bright light on it through a Wireless Assessment. A thorough audit of the WiFi 802.11 infrastructure equipment and an analysis of coverage and interference present within your office or campus. The Wireless LAN Assessment includes discovery of your access points, the access points near your office and detection of signal bleed outside the facility. A complete audit includes a wireless assessment checklist that will review all of the wireless infrastructure diagrams and wireless connection policies, security protocols that would be enforced, how many users are allowed to be associated with a specific access point and penetration testing to attempt unauthorized access to the wireless network. A Wireless Assessment will also analyze interference sources, including common problems like microwave machines, blue-tooth accessories such as wireless keyboards, wireless headsets and wireless pointing devices.
The assessment can be focused on a WiFi environment that is already in service or the wireless audit can be performed in a new WiFi environment where the client is looking for a wireless site survey, coverage recommendations and a final design of how many access points would be required and where they should be located. In the case where you are designing a new wireless environment, the assessment report would be written as a Bill-of-Materials and a technical description of the future security protocols and user density so that the WiFi network could be put out to bid to various WiFi manufacturers.
Why do you need a Wireless Assessment?
WiFi networks are becoming pervasive; in fact, many companies have deployed a WiFi network with little to no regard for securing their company LAN through the WiFi network. Many companies have such poor performing WiFi networks that employees take it upon themselves to go and buy $100 access points and bring them to work and hook their rogue access point up to your company LAN, without permission and without any security protocols enabled! The scary end result is that your company data is then available for any WiFi hacker to connect to the rogue access point and then get unfettered access to everything on your company LAN. So a Wireless Assessment can first and foremost, ferret out any rogue devices and then document the WiFi coverage and WiFi security posture of the wireless LAN.
Another motivating reason to perform a Wireless Assessment is because of the popularity of smart cell phones that have WiFi capabilities. Your employees have likely added your WiFi network access onto their phone without your approval or knowledge. The result is that your employees smart phones have uncontrolled and unsupervised access to your company LAN. The Assessment can document who is using your WiFi network and can provide some insight to what risks might be occurring at this moment.
Does Your Company have a WiFi Access Policy?
Your written IT security policies will define your organization's information security goals. At ANP we include a written security policy in every employee's employment agreement. In a changing IT environment, where new devices can gain access to your company LAN that are not controlled or owned by your company, businesses have rapidly changing information security needs. It's incumbent upon management to keep up with modern threats of WiFi information security and consider establishing a written WiFi policy as a guideline; regular policy review with WiFi experts will allow you to keep ahead of changes in the information landscape and address areas of concern before they become significant problems or worse yet you become a casualty of a WiFi data breach.
Wireless Infrastructure Threats:
The growing demand for wireless access has forced WiFi vendors to make an access point easy to setup. It is common for a wireless network to be added to existing infrastructure by following a setup wizard without much thought. This may be fine for a home network, but businesses have more at risk and need to ensure a secure and consistent implementation. One of the most common issues for wireless implementations are using weak encryption protocols like WEP or using weak Pre-Shared Keys for WPA2. As I mentioned earlier another common concern is someone installing an access point or wireless router on the network without company approval. This could be a misguided employee or an intentional malicious act. A third common issue is the improper configuration or no network access policy; for example a Guest wireless network that unintentionally allows access to internal LAN resources. You wouldn’t hang a live LAN cable out of your window, so make sure your wireless network is securely locked-up.
Wireless Site Survey Expertise:
The saying goes “you can judge a tradesmen by his tools,” goes a long way with WiFi consultants. The wireless assessment methodology that your IT Service Provider uses will tell you a lot about their expertise. Ask if your IT consultant has a Spectrum Analyzer that can detect out-of-band and in-band WiFi interference. An interference report is the most common problem with poorly performing WiFi infrastructure networks.
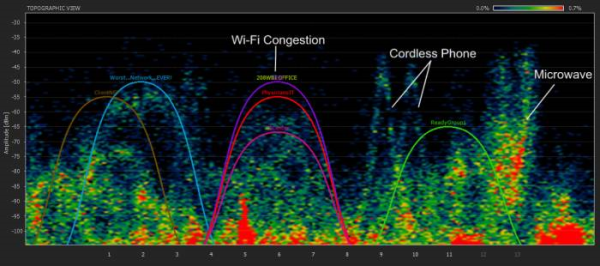
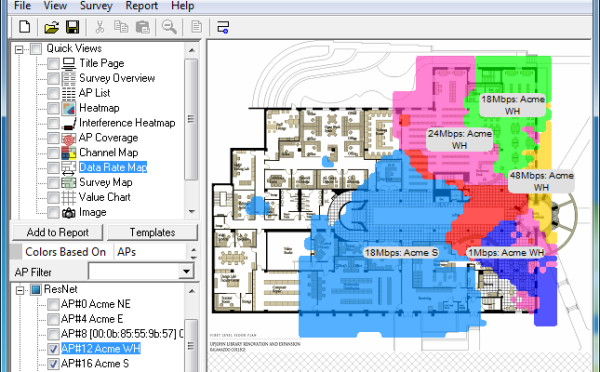
Insure that the consultant has a test set that uses your office floor plan. The consultant will load your floor plan in his test set and literally walk through your hallways, conference rooms and break rooms, he will also walk the outside of your building. The technician should also have an access point and multiple WiFi antennas and a tripod to hang-up and access point to simulate WiFi coverage in your office using various antennas to manipulate the signal coverage. The IT consultant should be able to produce WiFi reports that clearly documents the WiFi coverage of every access point in your office, look for a drawing that looks like this:
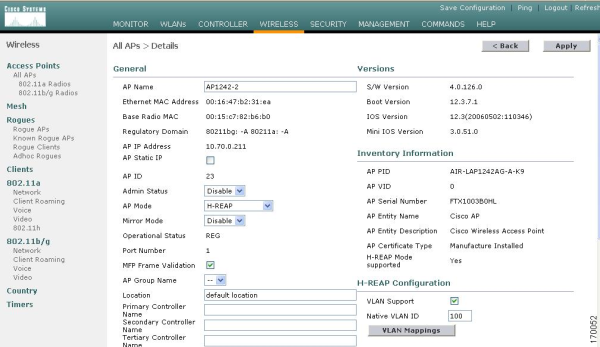
You are also going to need a list of detected access points, their security protocols and SSID names. The inventory report should look like something like this:
ANP’s TCP-IP security engineering team maintains a deep technical knowledge base of modern security threats. A Wireless LAN Assessment is more than wandering around with laptop looking for rogue access points or making sure your WiFi security keys are strong. The ANP engineering team understands wireless technology and can provide a comprehensive wireless audit by reviewing your security policies, your coverage densities, and then implement a complete wireless network not just some helter-skelter access points.
Would you like to learn more? Follow this link to our WiFi Assessment page to discuss your needs. During this Halloween holiday let’s give the boot to the Ghouls, Ghosts and Goblins; and kick them out of your Wireless LAN!

